However personal mobile devices don t offer the same level of built in security or control as the organization owned desktop computers they are replacing.
Mobile device security threats and controls.
This is exactly where google and apple lack control he adds.
Mobile threat researchers identify five new threats to mobile device security that can impact the business.
Here are some practical steps that will help you minimize the exposure of your mobile device to digital threats.
With the number of types of smart devices from rfid chips to thermostats and even kitchen appliances growing so quickly they can t always be monitored.
They include application based web based network based and physical threats.
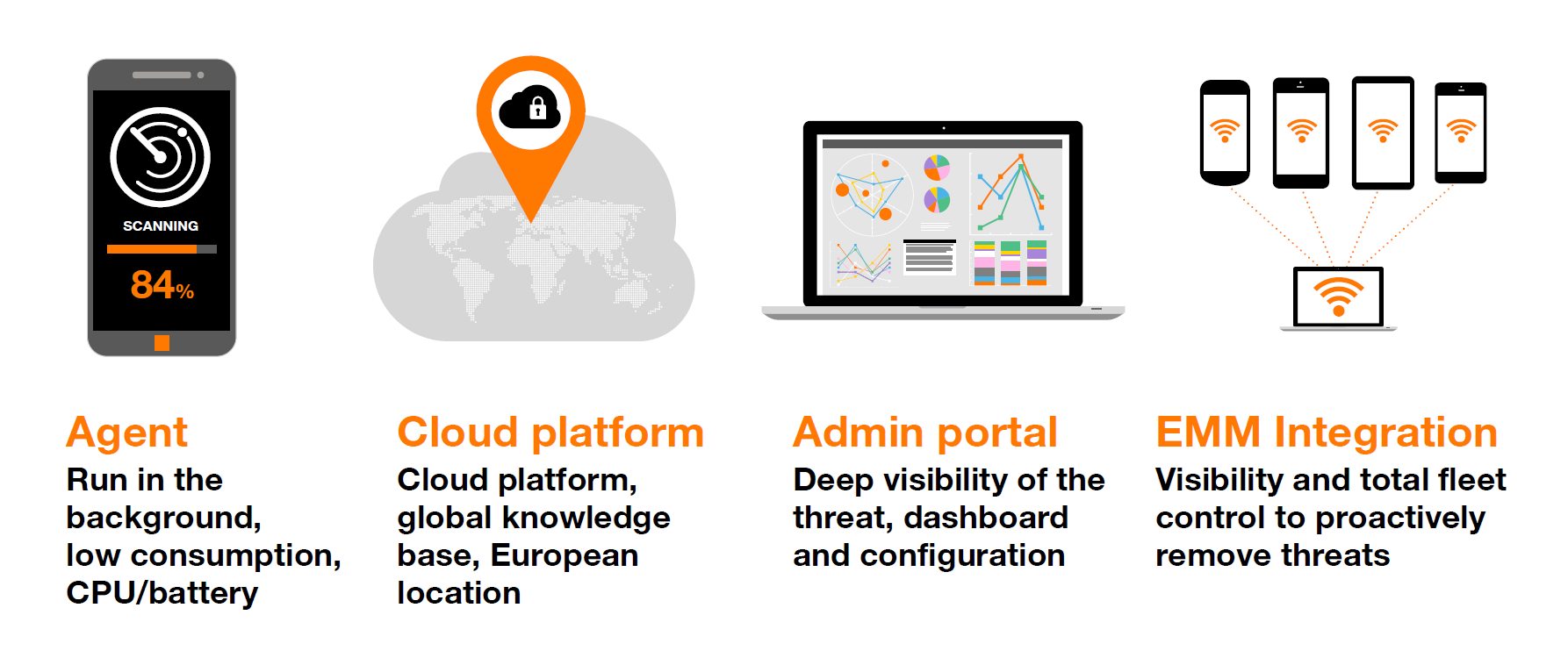
Learn about the enterprise mobile device security controls including malware defense threat detection and centralized management that you should consider when formulating an enterprise.
Application based threats web based threats network based threats and physical threats.
Here s how they work.
Some of the security threats include malware specifically designed for mobile devices i e.
The internet of things iot.
Worms and spyware unauthorized access phishing and theft.
But not all is lost.
Like viruses and spyware that can infect your pc there are a variety of security threats that can affect mobile devices.
People tend to look at mobile security threats as an all encompassing threat.